In CyberNEMO, we’re building a Zero Trust Network Access (ZTNA) solution where every decision is backed by verifiable evidence. Beyond authenticating users and devices, we also need to ensure that the network paths packets take can be trusted. That’s where the Proof of Transit (PoT) component comes in.
What is the Proof of Transit (PoT)?
PoT, is a path verification mechanism. Its purpose is to guarantee that a packet has followed a predetermined route through specific nodes, providing security, traceability, and regulatory compliance.
This capability is essential in environments such as:
-
Service Function Chaining (SFC) with NFV
-
5G and beyond network architectures
-
Critical infrastructure where packet order and integrity must be preserved
PoT ensures that packets not only arrive at their destination but also travel through the expected, authorized sequence of nodes.
How it Works?
The IETF PoT draft defines two main approaches, both based on Shamir Secret Sharing (SSS):
1.Polynomial-based distribution:
-
A polynomial of degree n–1 (where n is the number of nodes) is generated.
-
Each node receives a point on the polynomial, used to verify its participation in the path.
2.Enhanced entropy with a public polynomial:
-
An additional polynomial (with no constant term) is introduced.
-
This is combined with a random value (RND) at the ingress node, creating a cumulative value (CML).
-
The value travels across all nodes, and the final node verifies it against the expected result, ensuring no tampering occurred.
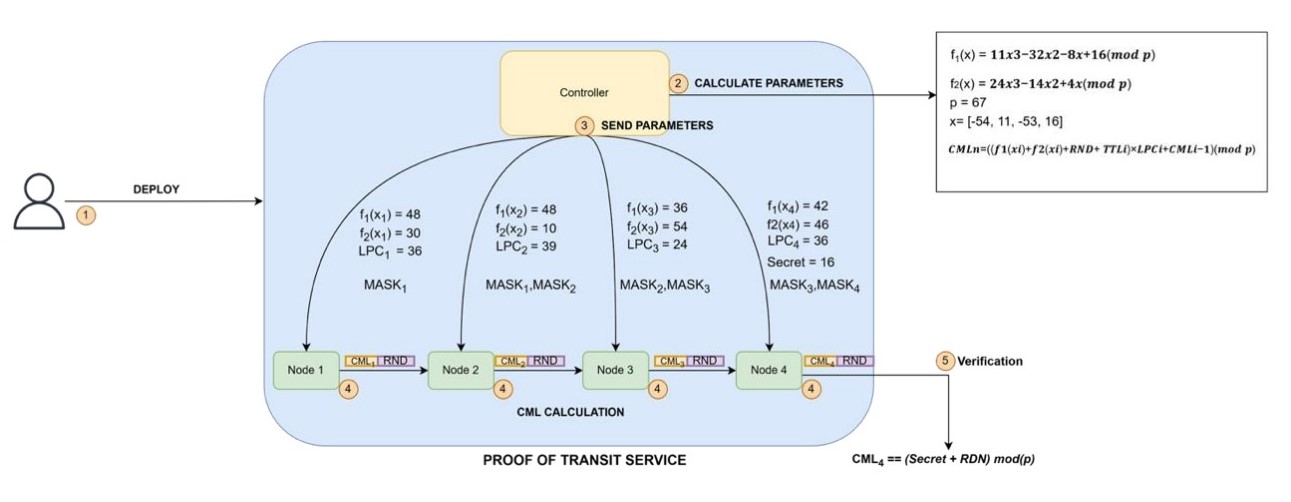
Ordered Proof of Transit (OPoT)
PoT has naturally evolved into OPoT (Ordered Proof of Transit), which not only validates the nodes traversed but also guarantees the correct sequential order. This prevents reordering attacks and is particularly critical in Real-time, sequence- sensitive systems.
OPoT achieves this by using symmetric masks shared between contiguous nodes,
ensuring both authenticity and ordering of packets.
Why this matters for ZTNA
ZTNA is about “never trust, always verify.” Proof of Transit extends this principle to the network fabric itself. By integrating PoT and OPoT into CyberNEMO, we:
-
Ensure packets take only the approved, policy-compliant paths
-
Detect tampering, misrouting, or reordering of traffic
-
Provide strong traceability and auditability of packet flows
-
Meet compliance and regulatory requirements for sensitive environments
In other words, PoT brings verifiable trust to packet transit, strengthening the Zero Trust foundation of CyberNEMO.

